TamilCTF September Event
Reverse Engineering Challenges:
Digital Play
DESCRIPTION : My friend made this encryption circuit to encrypt the text. Could you help to decrypt that text.
AUTHOR : 0xrakesh
FILE : encrypt.dig, enc.txt.
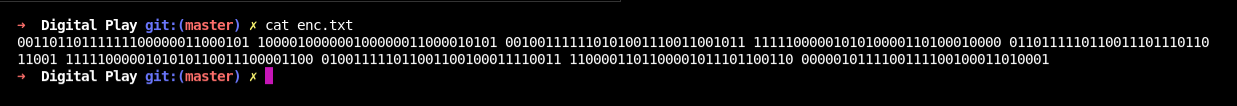
Enc.txt
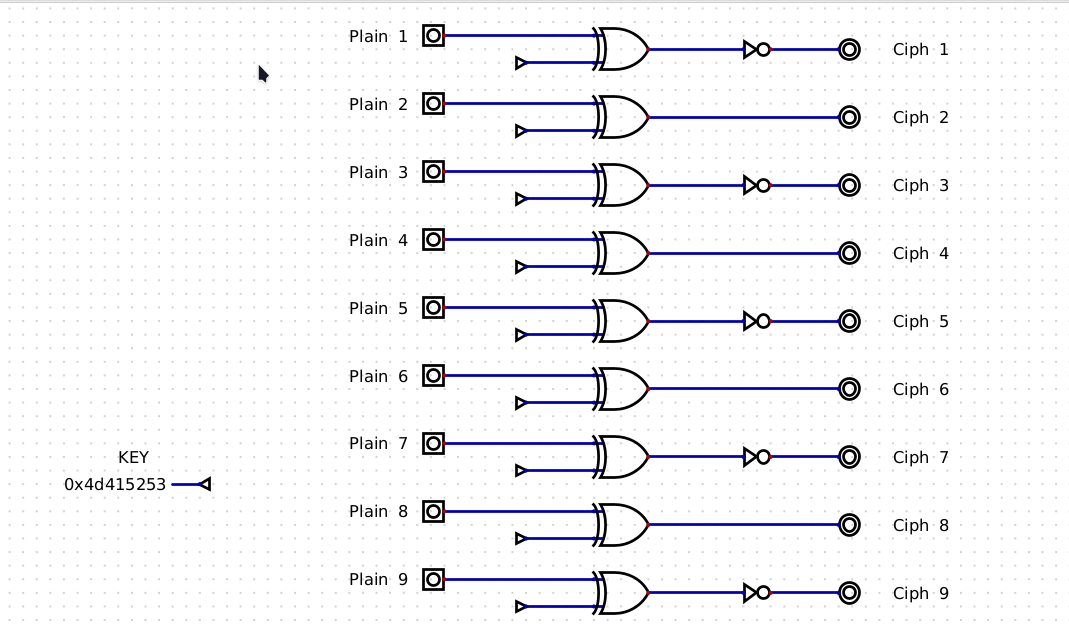
Encrypt.dig
The Plain text is xor with key and inverse the even number plain text.
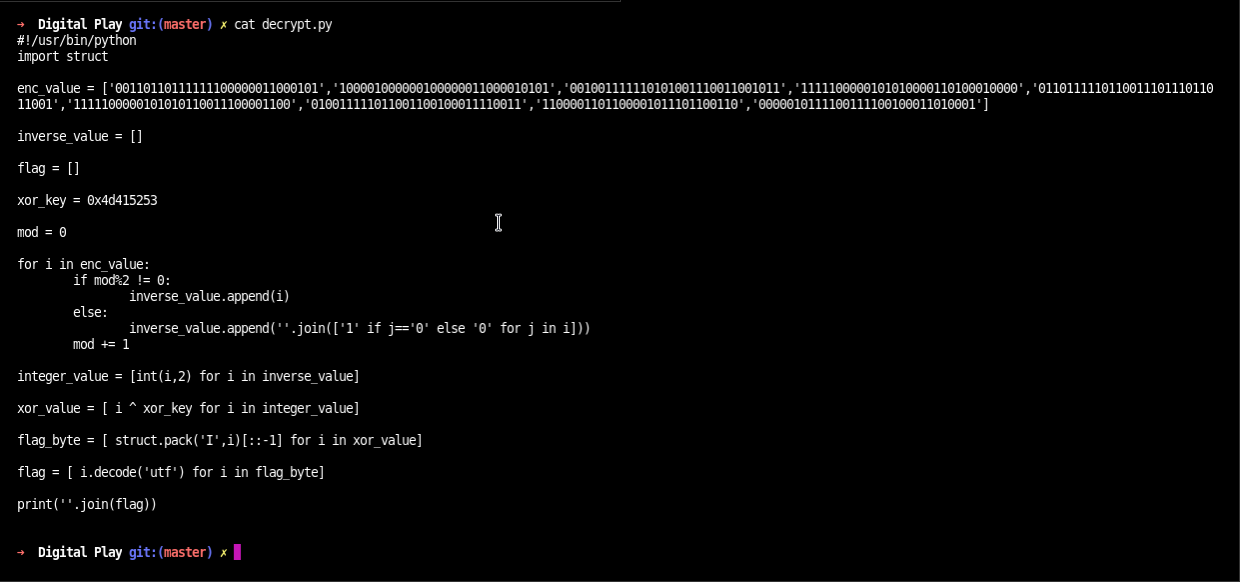
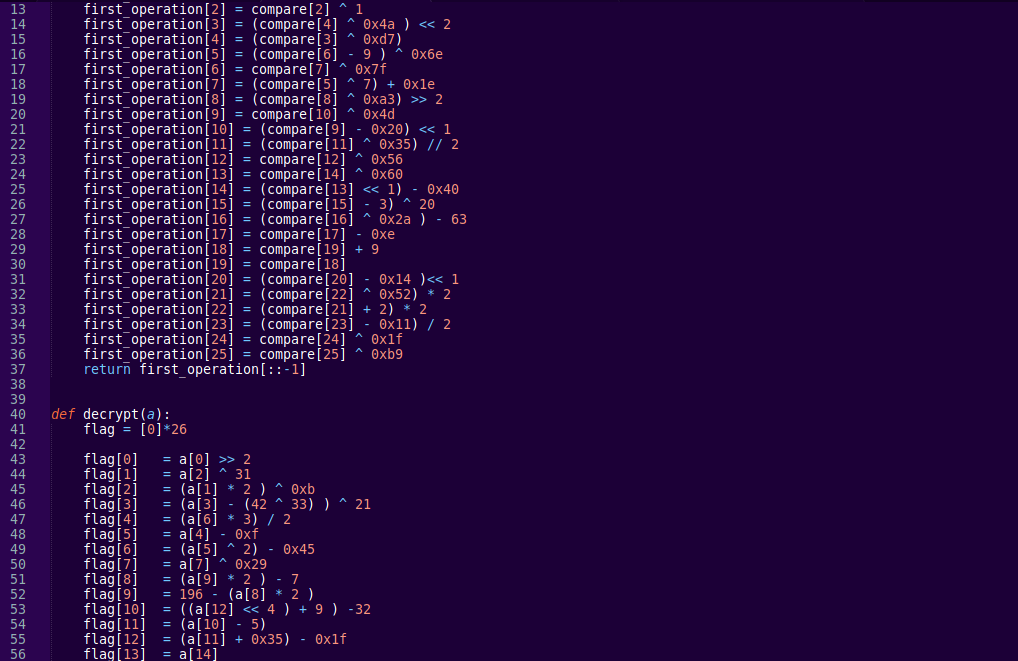
Let make an decrypt script:
- Inverse the even number encrypt text.
- Change the binary number to integer number.
- Xor the integer number with xor key (0x4d415253).
- Then unpack the hex value with the help of struct module.
- Finally change the byte text to string
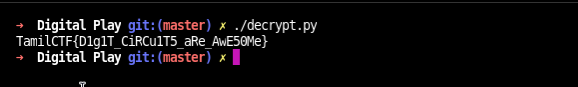
Run the script
Flag is TamilCTF{D1g1T_CiRCu1T5_aRe_AwE50Me}
Eezy
DESCRIPTION : Don't try to debug me :( . You can't bypass me. Lets see if you can.
AUTHOR : 0xrakesh
FILE : challenge
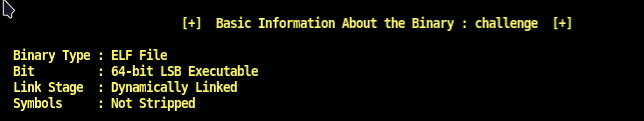
Basic Info:
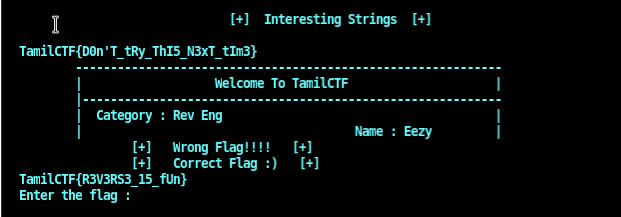
Interesting strings:
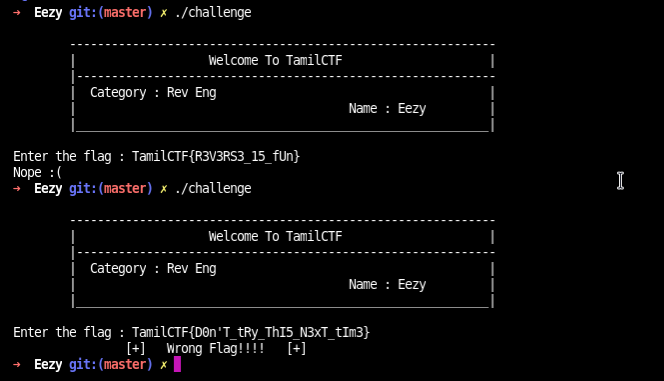
Run the binary:
Ghidra
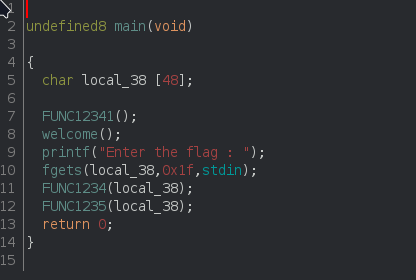
Analysis the binary in ghidra. The main function:
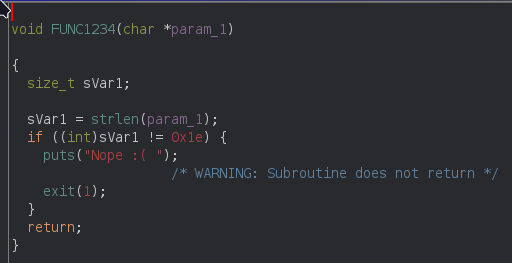
The program takes a flag and call the FUNC1234 function. The FUNC1234 function:
The FUNC1234 function check the length of flag.
The Length of the flag is 0x1e (30). After this function , it call the FUNC1235 function.
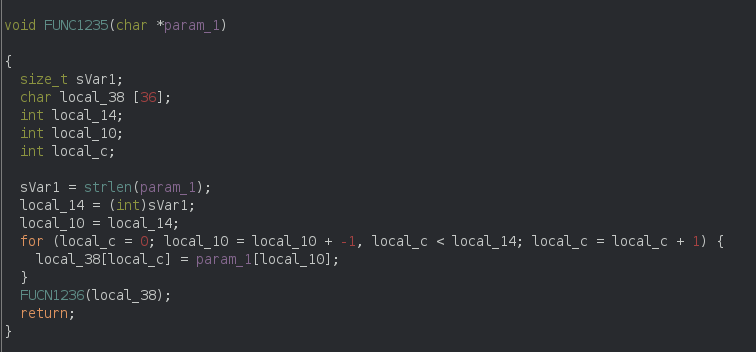
The FUNC1235 function:
The FUNC1235 function inverse the flag. And call the FUNC1236 function with argument of inversed flag.
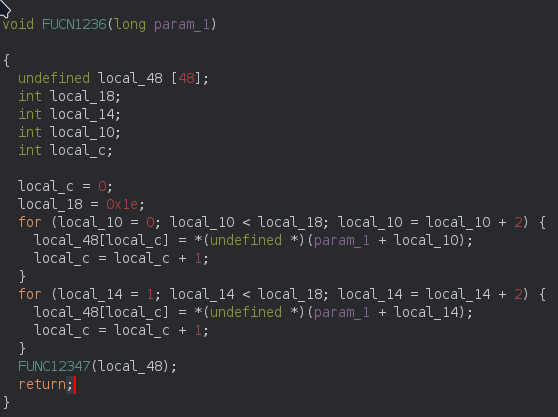
The FUNC1236 function:
The FUNC1236 function shuffle the flag. There are two flag, the first loop store even value of flag in new variable and the second loop store odd value of flag in new variable. And call the FUNC123 with the argument of new variable.
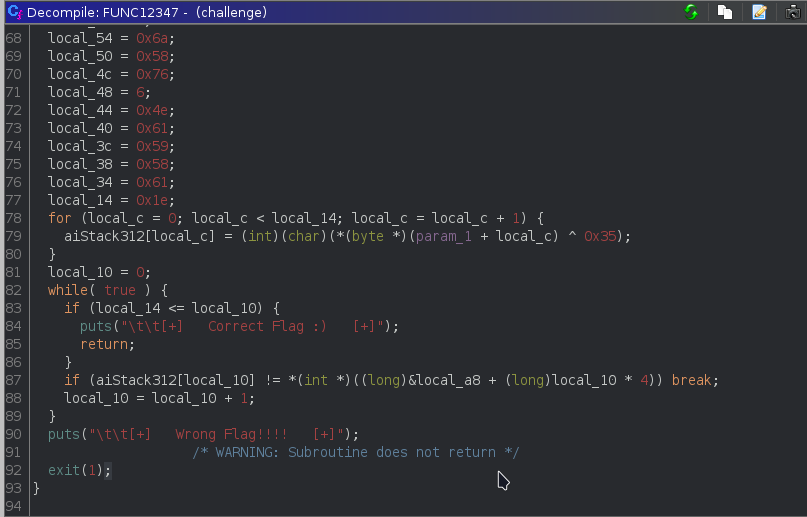
The FUNC1237 function xor the shuffled flag with 0x35 and check with some values.
Lets make a script
- Xor the check value with 0x35.
- Shuffle the xored value.
- Inverse the value.
Run the script:
Flag is TamilCTF{W3lC0m3_T0_tAm1lCtF!}
Guesser
DESCRIPTION : My friend make a secure login app. It contain the secret message. Can you break the app and get the secret message for me :/
AUTHOR : 0xrakesh
FILE : Guesser
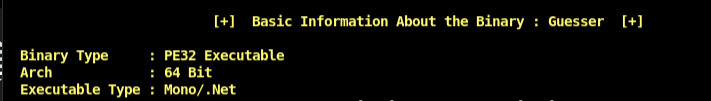
Basic Info:
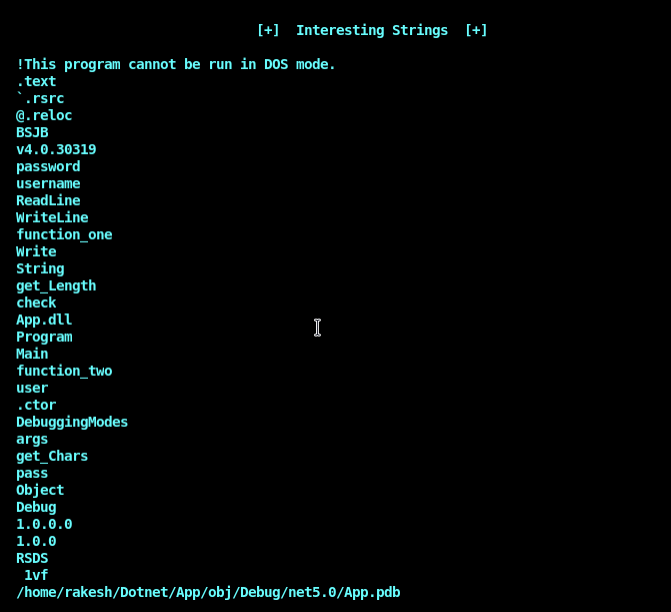
Strings:
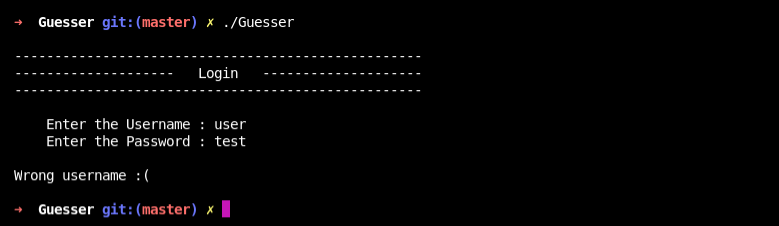
Run the binary
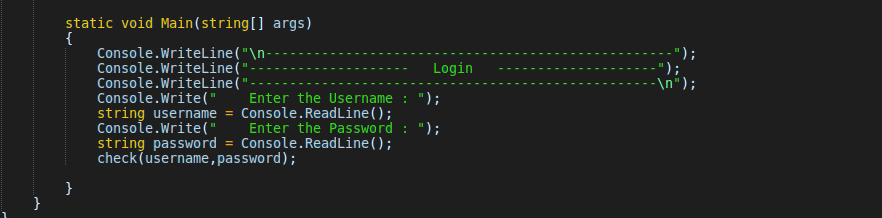
It ask for username and password.
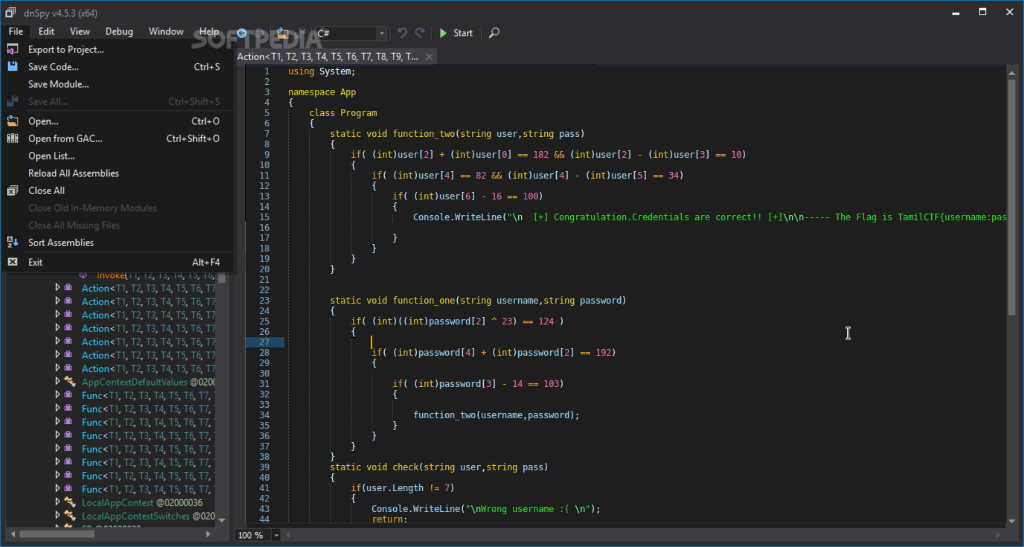
Open the file in DNSpy
Every C# program start with main function.So Look at the main function
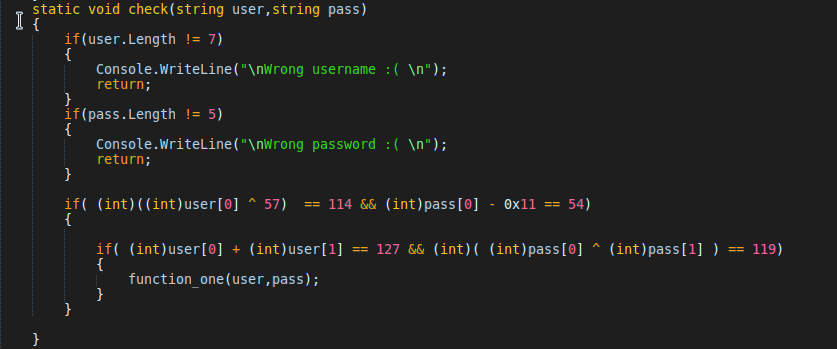
It get username and password, then call the check function with argument of username and password.
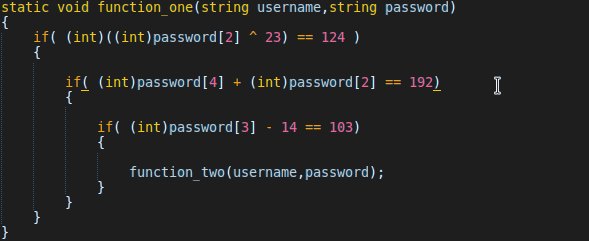
It check the length of username and password. The username's length must by 7 and the password's length must be 5. If it's equal, then it do some operation and check with some value. After the check function, it call the function_one function with the argument of user and pass.
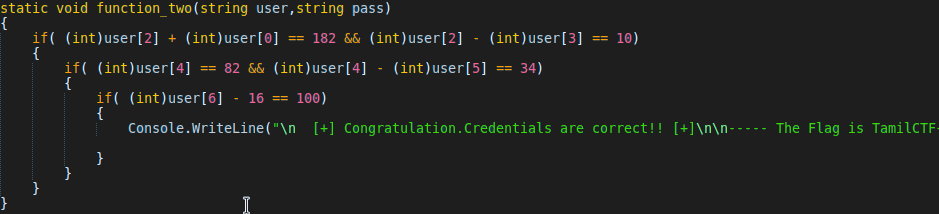
Same as check function, it also do some operation with password and check with some value. And call the function_two function with the argument of username and password.
It check the username with some value. If it is equal, it print the congratulation message.
Lets make a script:
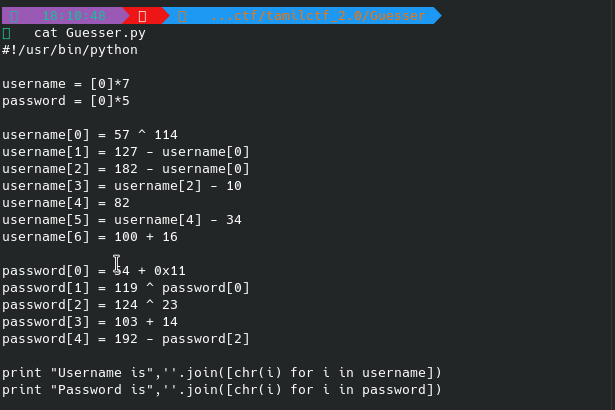

Run the script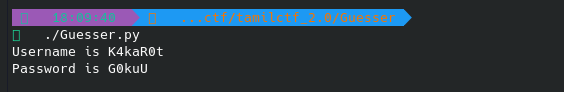

Confirm the username and password is correct or not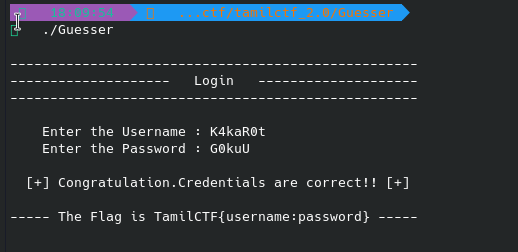

Yeah!!!! The username and password are correct!!! :)
Flag is TamilCTF{K4kaR0t:G0kuU}
Unknown
DESCRIPTION : Is this file a binary in disguise?
AUTHOR : 0xrakesh
FILE : challenge
Analysis the file
file challenge
strings challenge
There is no interesting string in this binary.
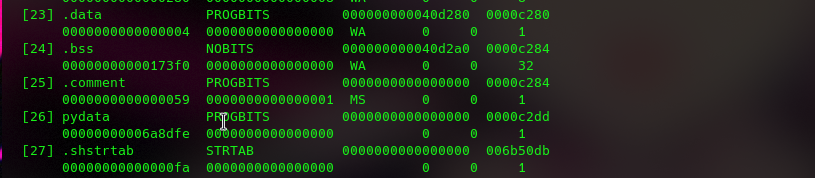
readelf -S challenge
The Challenge binary contain the pydata section. So it is python file that compilt to elf. So decompile this file by using pyinstxtractor.
pyintxtractor.py challenge
It gives the python bytecode.
uncompyle6 challenge.pyc
It gives the python file.
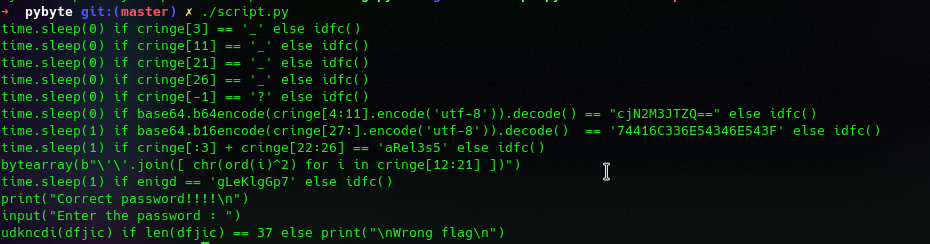
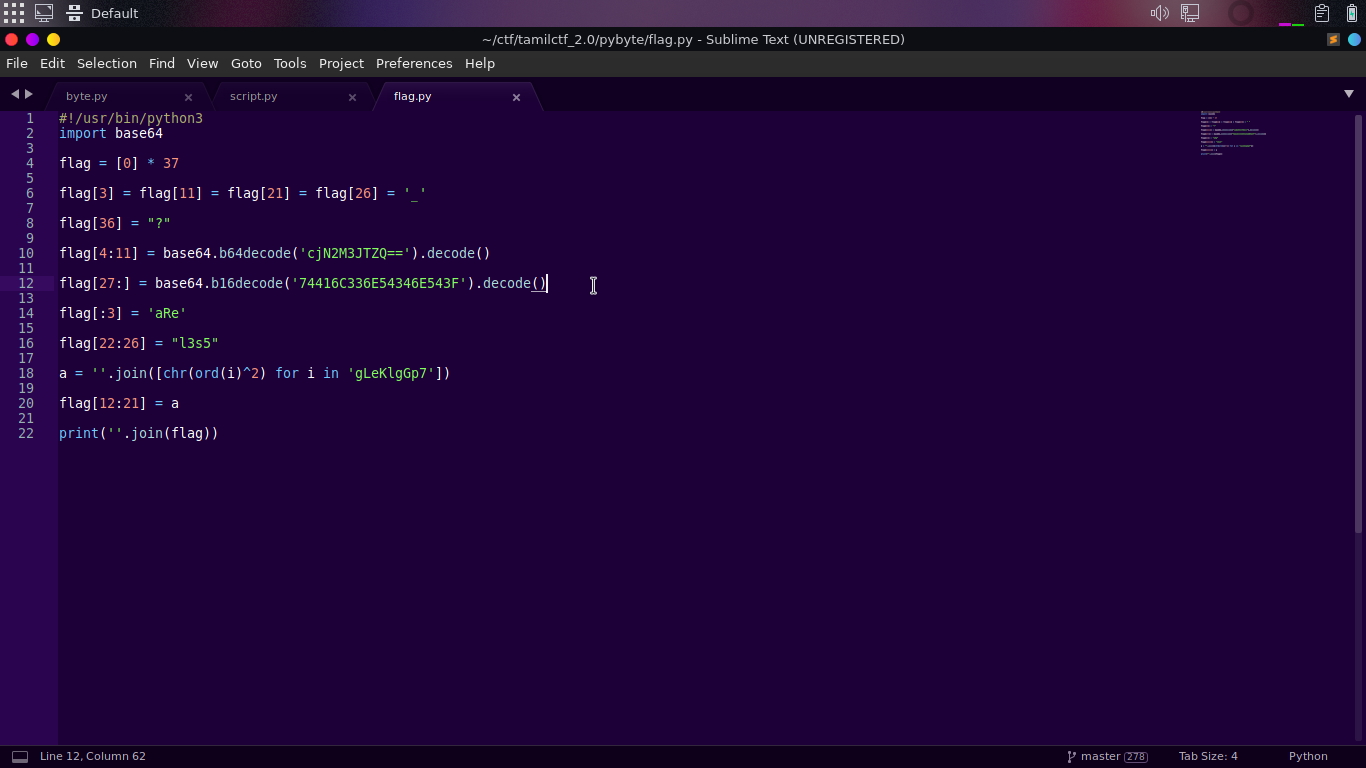
Python Script
The lines are encode by bytearray and execute by using eval(). To decode the line, we just replace the eval() to print().
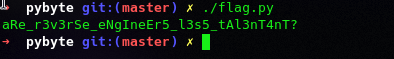
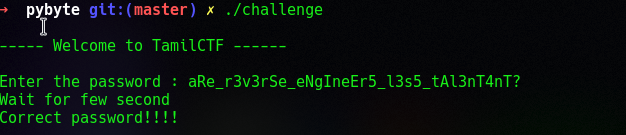
Run the script
Lets make a script to decode
Output
Check the output is correct or not
The flag is TamilCTF{aRe_r3v3rSe_eNgIneEr5_l3s5_tAl3nT4nT?}.
Hey I'm AB
DESCRIPTION : My phone got crashed and I took a backup of some important data.
AUTHOR : Abhi
FILE : android.ab
Basic Info
The .ab file is android backup file. Lets extract the file
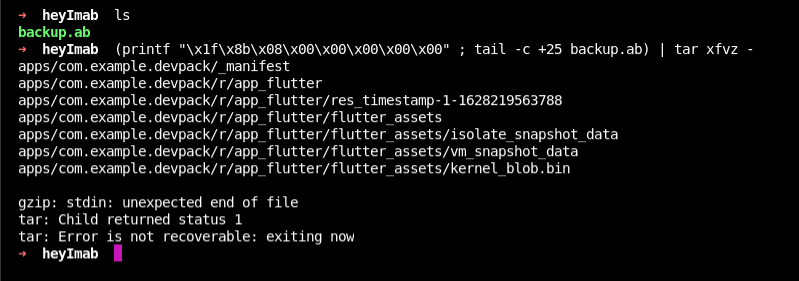
(printf "\x1f\x8b\x08\x00\x00\x00\x00\x00" ; tail -c +25 backup.ab) | tar xfvz -
List out the files

Cat the all files with grep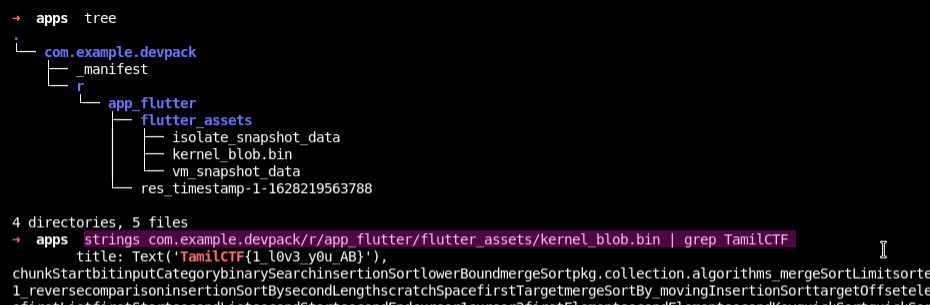

The flag is : TamilCTF{1_l0v3_y0u_AB}
Obscure
DESCRIPTION : Be a nerd coder and little bit of hacker
AUTHOR : aidenpearce369
FILE : obscure
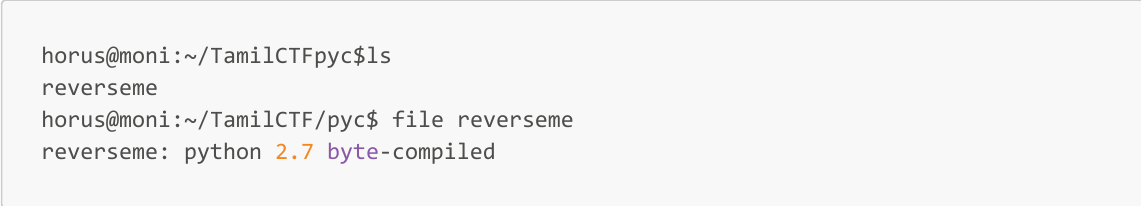
Basic Info
file reverseme
So it is a byte-code file from python 2.7.
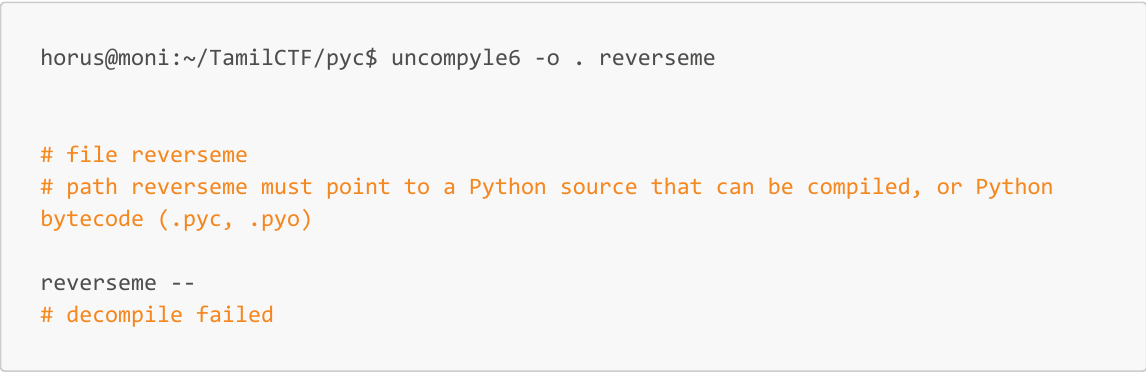
Lets try to decompiling the file to its own python file by uncompyle6.
To decompile the file, just rename the reverseme to reverseme.pyc
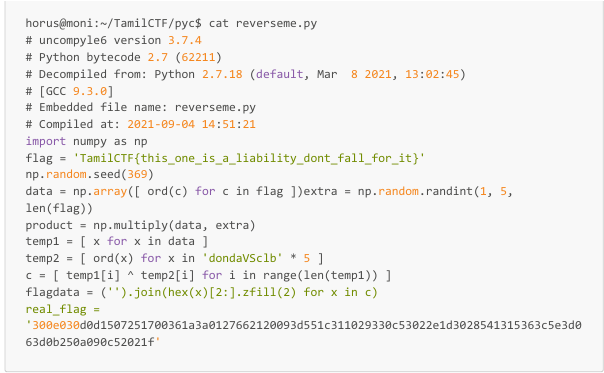
Lets look at the script
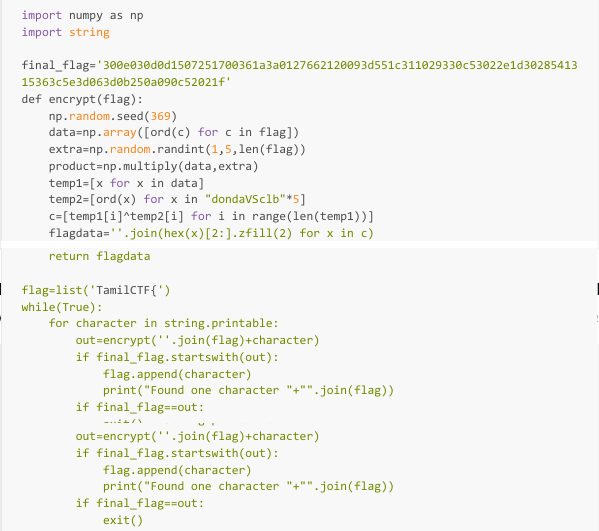
So in this python script an obfuscated output is produced from the string. And our string is a fake flag. But the output is produced from each characters in the flag. And there is an obfuscated value for the real flag, we have to just reverse it to its characters. By checking the output for the string "TamilCTF{" it gives the obfuscated value as "300e030d0d15072517" which is also present in real flag.
All we have to do is perform the obfuscation mechanism for each character and compare it with the real_flag , which is moreover a bruteforce attack.
Lets make a script
Run the script
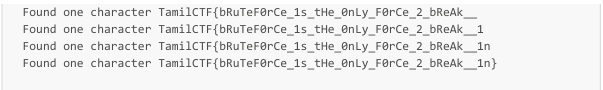
The flag is TamilCTF{bRuTeF0rCe_1s_tHe_0nLy_F0rCe_2_bReAk__1n}
Foolme
DESCRIPTION : Make a call :) , But it not a pwn challenge.
AUTHOR : 0xrakesh
FILE : foolme
HINT : Don't try automation. The flag will be meaningful text. Did you play my EeZY reverse challenge?
Basic info
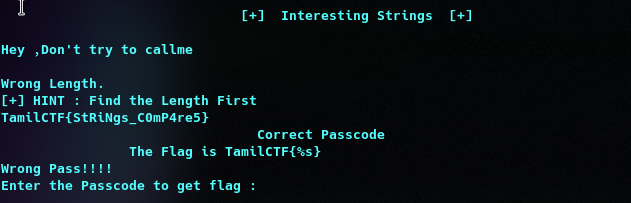
Interesting string
There is one interesting string ( TamilCTF{StRiNgs_C0mP4re5} )
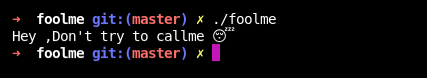
Run the binary
Open the binary in binaryninja
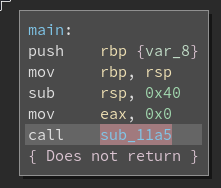
The main function call the sub_11a5 function and it does not return .
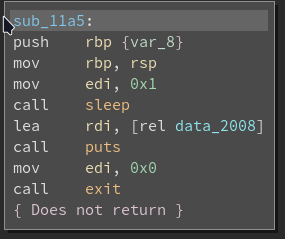
The sub_11a5 function sleep for 1 second and exit the program. So we need to bypass the sub_11a5 function by convert the call instruction to nops .
Step : Right click the call instruction -> Patch option -> convert to Nop.
After the convert the call instruction to nops , just save the binay.
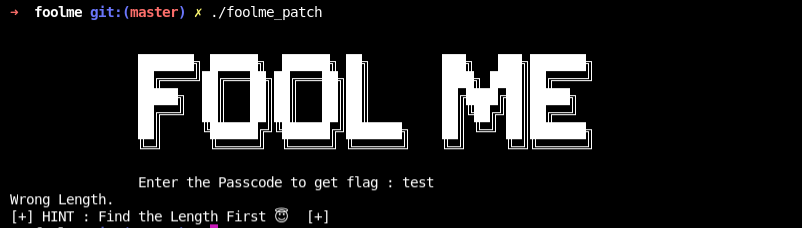
Execute the patch binary
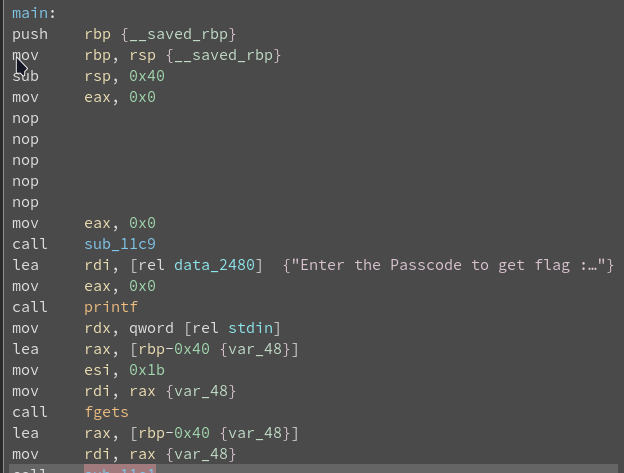
It ask for passcode to get the flag. Then print Wrong Length and find the length first.
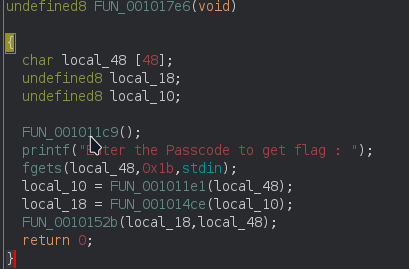
Analysis the file in Ghidra
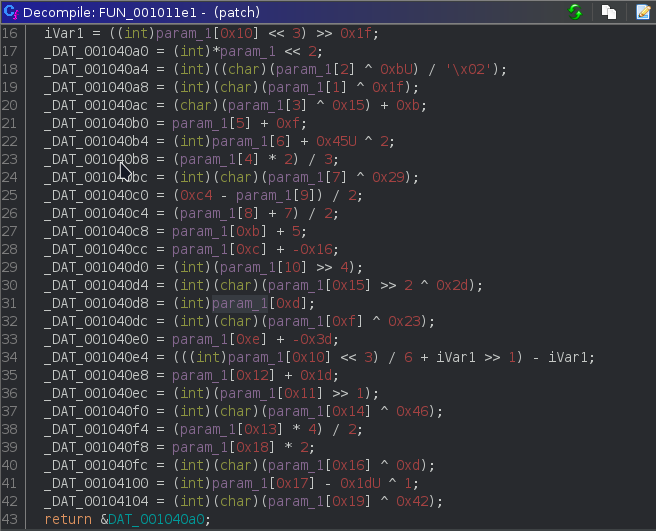
It takes a user input and call the three function. The first function do some operation with user input and return the value.
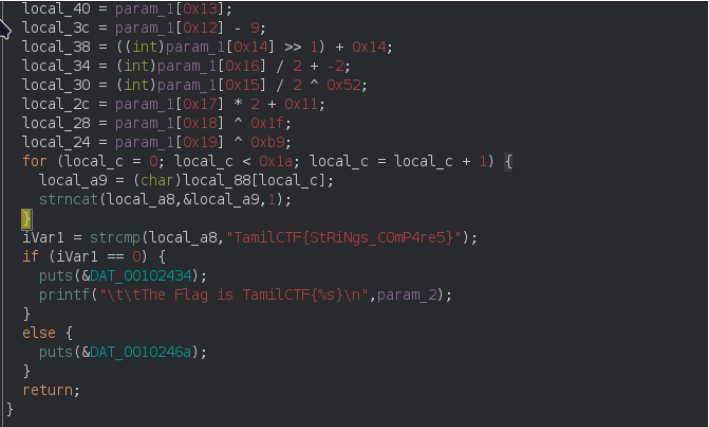
The second function inverse the user input and return the value.
The third function ( FUN_0010152b ) do some operation as same as first functionand finally the value is compare with TamilCTF{StRiNgs_C0mP4re5} .If it’s equal ,it print “Correct Flag” , otherwise it print “Wrong Flag”.
Lets make a script
- We have the compare string (TamilCTF{StRiNgs_C0mP4re5}) , just reverse the operation.
- Change the string into integer and store list.
- Reverse the operation done in third function and return the inverse value.
- Reverse the First function operation and print the flag as string.
Run the script
1.As we already know that the flag is meaningful text.
2.And Hint is “Did you play my EeZY reverse challenge?”.
r3vErrE ---> r3vErsE
eZP ----> eZY
15_tH15_eZY_r3vErsE_cHalL?
Test the passcode
The flag is TamilCTF{15_tH15_eZY_r3vErsE_cHalL?}